This document provides facts related to SAML for usage in the written part of my diploma thesis.
 Security Assertion Markup Language
Security Assertion Markup Language SAML 1.0 since 5/2002
SAML 1.0 since 5/2002 SAML 1.1 since 9/2003
SAML 1.1 since 9/2003 provides a means of expressing information about authentication and authorization, as well as attributes of an end user (for example, a credit limit) in XML format [On02]
provides a means of expressing information about authentication and authorization, as well as attributes of an end user (for example, a credit limit) in XML format [On02] defines syntax and semantics of XML-encoded assertion messages [Sh03]
defines syntax and semantics of XML-encoded assertion messages [Sh03] defines request and response protocols between requesting and asserting parties for exchanging security information [Sh03]
defines request and response protocols between requesting and asserting parties for exchanging security information [Sh03] defines rules for using assertions with standard transport and message frameworks. For example, it defines how SAML assertion messages can transport using SOAP over HTTP [Sh03]
defines rules for using assertions with standard transport and message frameworks. For example, it defines how SAML assertion messages can transport using SOAP over HTTP [Sh03] SAML data may be inserted into a SOAP message using the WS-Security framework [On02]
SAML data may be inserted into a SOAP message using the WS-Security framework [On02] used to express information about an act of authentication or authorization that has occurred in the past (does not provide authentication) [On02]
used to express information about an act of authentication or authorization that has occurred in the past (does not provide authentication) [On02] If an entity is authorized based on the fact that they were previously authorized by another system, this is called "portable trust". [On02]
If an entity is authorized based on the fact that they were previously authorized by another system, this is called "portable trust". [On02] By authenticating once, being authorized, and effectively reusing that authorization for subsequent Web Services, single sign-on for Web Services can be achieved. [On02]
By authenticating once, being authorized, and effectively reusing that authorization for subsequent Web Services, single sign-on for Web Services can be achieved. [On02] SAML request/response protocol [Sh03]:
SAML request/response protocol [Sh03]: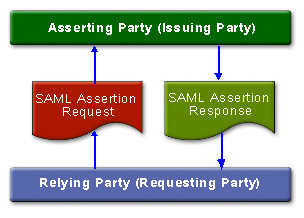
| Article found | Fact |
|---|---|
Web Service Security [On02]
| Note that this information in a SAML assertion may not indicate the end user's identity. The user may have authenticated using a username and password, and the administrator of the Web site may have no idea of the user's actual identity. It may simply be an indication that the user presented credentials and was authenticated and authorized. SAML allows information to be placed into a SOAP message to say "this person was authorized according to a certain security policy at a certain time." If the recipient of this SOAP message trusts the issuer of the SAML data, the end user can also be authorized for the Web Service. This SAML data is known as an "assertion" because the issuer is asserting information about the end user. The concept of security assertions has existed before SAML, and is already widely used in existing software. |
| Security for Parlay-X - challenges and solutions [Eckardt] |
|
Secure Web services [Sh03]
|
|
| Article found | Sample |
|---|---|
Secure Web services [Sh03]
|
|
| Article found | Sample |
|---|---|
Secure Web services [Sh03]
|
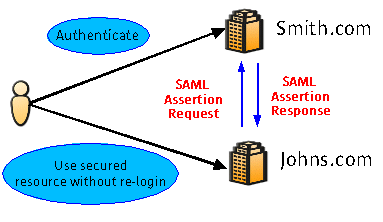
Suppose a user logs in to Smith.com and is authenticated. Later, the same user accesses Johns.com. Without single sign-on, the user would typically have to reenter his user identity information to Johns.com. Under the SAML scheme, by sending an SAML assertion request message, Johns.com can ask Smith.com if the user has already been authenticated. Smith.com then sends back an SAML assertion statement indicating that the user in fact has been authenticated. Once Johns.com receives the SAML assertion statement, it allows the user to access its resources without asking the user to reenter his identity information. |
| Article found | Sample |
|---|---|
Secure Web services [Sh03]
|
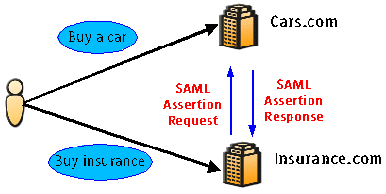
In this case, let's say a user buys a car from Cars.com. The same user then decides to buy automobile insurance from Insurance.com. Now, when the user goes to Insurance.com to buy insurance, the user's profile such as name, address, and credit history, which Cars.com has already collected, can pass to Insurance.com. In this case, Insurance.com sends an SAML assertion request, such as, "Send me user profile information," to Cars.com, and Cars.com sends all the user profile information it knows to Insurance.com in SAML assertion statements. |
| Article found | Sample |
|---|---|
Secure Web services [Sh03]
|
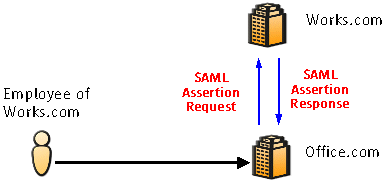
Let's say a Works.com employee named Sang wants to order $1 million worth of furniture from Office.com, Works.com's preferred furniture supplier. When Office.com receives the purchase order from Sang, obviously it wants to know if Sang is authorized to complete the order and, if so, the maximum dollar limit he can spend. So in this scenario, when Office.com receives a purchase order from Sang, it sends an SAML assertion request message to Works.com, which then sends back an SAML assertion indicating that Sang in fact is allowed to order the furniture, but the maximum amount he can spend is $1,000. |
| Article found | Sample |
|---|---|
| Secure Web services [Sh03] |
An authentication statement basically says that an issuing authority (asserting party) asserts that a subject S was authenticated by M's authentication means at time T. As you probably guessed, the authentication statement is used to enable single sign-on. SAML assertion containing an authentication statement: <saml:Assertion ...> <saml:AuthenticationStatement AuthenticationMethod="password" (By means M) AuthenticationInstant="2001-12-03T10:02:00Z">(At time T) <saml:Subject> (Subject S) <saml:NameIdentifier SecurityDomain="sun.com" Name="Sang" /> <saml:ConfirmationMethod> http://...core-25/sender-vouches </saml:ConfirmationMethod> </saml:Subject> </saml:AuthenticationStatement> </saml:Assertion>In this Sample, the authentication statement (SAML assertion response message) says that a subject called Sang in security domain of sun.com has been authenticated at some time on December 3, 2001. The means of authentication is the entering of username and password. |
| Secure Web services [Sh03] |
An attribute SAML statement indicates that an issuing author asserts that a subject S is associated with attributes A, B, and so on, with corresponding values a, b, and so on. An attribute statement is useful for distributed transactions and authorized services. SAML statement with attribute statements: <saml:Assertion ...> <saml:AttributeStatement> <saml:Subject> ..Sang.. </saml:Subject> <saml:Attribute AttributeName="PaidStatus" (attribute A) AttributeNamespace="http://smithco.com"> <saml:AttributeValue> (with value a) PaidUp </saml:AttributeValue> </saml:Attribute> <saml:Attribute AttributeName="CreditLimit" (attribute B) AttributeNamespace="http://smithco.com"> <saml:AttributeValue> (with value b) <my:amount currency="USD"> 500.00 </my:amount> </saml:AttributeValue> </saml:Attribute> </saml:AttributeStatement> </saml:Assertion>This Sample contains two attribute statements (SAML assertion response message) for a subject Sang. The first attribute has the name PaidStatus, with corresponding value paidup. The second attribute has the name CreditLimit, with corresponding value of 500.00. This assertion could be used for the third use-case, where a Works.com employee tries to purchase $1 million worth of chairs from Office.com. |
| Secure Web services [Sh03] |
An authorization statement is the third kind of SAML assertion statement. This type of statement says that an issuing authority decides whether to grant the request by subject S for access type A to resource R, given evidence E presented by the requesting party. The resource can be a Web service or Webpage. Authorization statement in an SAML assertion: <saml:Assertion ...> <saml:AuthorizationStatement Decision="Permit" (Whether to grant request) Resource="http://jonesco.com/rpt_12345.html"> (for res. R) <saml:Subject> ... Sang ... </saml:Subject> (by Subject S) <saml:Actions ActionNamespace="http://...core-25/rwedc"> <saml:Action> Read </saml:Action> (for access type A) </saml:Actions> </saml:AuthorizationStatement> </saml:Assertion>This Sample's SAML assertion contains a single authorization statement (SAML assertion response message). The resource is a Webpage whose address is http://jonesco.com/rpt_12345.html. In this example, after receiving an SAML assertion request message with some kind of evidence E, an asserting party grants the request, indicating that the subject Sang can read the Webpage. |