| Article found | Fact |
|---|
|
Web Service Security [On02]
|
- Web Services present a new avenue of attack into the enterprise.
- some of the tactics are familiar: feeding unexpected data to an application in order to confuse it, or disable it
- Details of WSDL-files can be used to attack with inappropriate data
- It is important, therefore, that "sanity checks" are performed on incoming data directed to Web Services (f.e. against the XML-Schema)
- XML Schema validation is processor-intensive
- In addition, certain portions of a SOAP message may be volatile,
meaning that they change while in transit between the SOAP requester and the Web
Service. Volatile portions of a SOAP message include the header, which may contain
routing information that changes as the message is routed
- Another aspect of content filtering is ensuring that only valid Web Services are
called. Firewalls must be able to distinguish SOAP requests from invalid requests
|
|
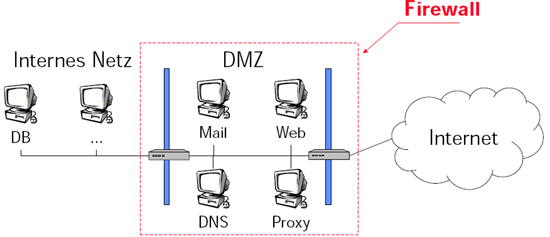
Sicherung von Web Services durch Firewalls [JZ03]
|
- Vorteile:
- Paketfilterung weit verbreitet (Router, kommerzielle und freie Produkte)
- Einfacher Paketfilter arbeitet sehr effizient
- Nachteile:
- Filterregeln oft schwer konfigurierbar und testbar
- Komplexe Filter erzeugen Last
- Nicht alle Policies durch Filterregeln durchführbar
(z.B. Benutzerauthentisierung); hier Einsatz von intelligenten Filtern nötig
|