This document provides facts related to a combination of several security standards for usage in the written part of my diploma thesis.
| Article found | Fact |
|---|---|
| Secure Web services [Sh03] |
The SAML assertions can be digitally signed using XML digital signature. The same assertions can be encrypted using XML Encryption to ensure privacy. The public key used for digital signing and encryption can be validated and registered via XKMS. As for XACML, an SAML asserting party could use it to define an access control policy as a basis for handling SAML-based assertion requests.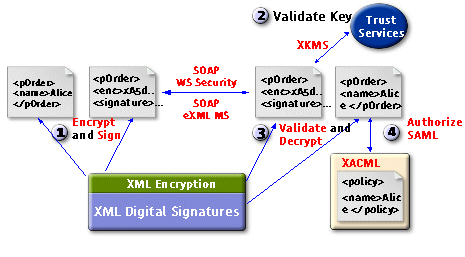 On the left side of the diagram, Alice uses XML digital signature and encryption to digitally sign and encrypt the purchase order XML document. She then sends the document to her supplier, perhaps using SOAP, whose header structure is defined either in the WS-Security or ebXML Message Service standard. The document's receiver then could use XKMS to look up and validate Alice's public key. Once the key is determined trustworthy, the receiver then validates and decrypts the purchase order. Finally, the receiver checks a policy server for authorization by sending and receiving SAML requests and responses. The policy server might maintain the access control policy information in XACML. |