| Article found | Fact |
|---|
|
Web Service Security [On02]
|
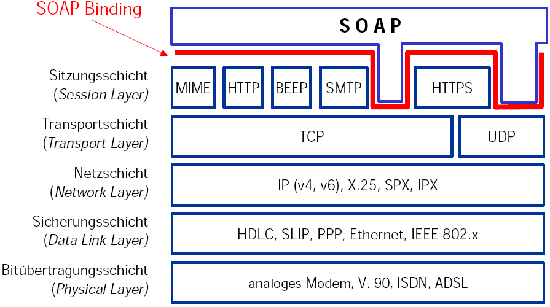
- [...] independent
of the underlying communications layers. Many different communications technologies
can be used in the context of one multihop SOAP message; for example, using HTTP
for the first leg, then SMTP for the next leg, and so forth. End-to-end security cannot
therefore rely on a security technology that presupposes one particular communications
technology
- [...] transport-level security only deals with the originator of the SOAP request. SOAP
requests are generated by machines, not by people. If the Web Service wishes to
perform security based on the end user, it must have access to authentication and/or
authorization information about the end user on whose behalf the SOAP request is
being sent.
- (both mentioned reasons applie to SOAP-messages that are routed between Web Services too ("multiple connections"))
|