 Exploitation Tool of Choice for Internet Hackers Everywhere by Steve Gibson, Gibson Research Corporation Page last modified: Oct 06, 2003 at 13:31 |
 Photo created by Karen Eliot. Used with permission.
Page Updates & News:
With all due respect to Microsoft, I believe that either the right people within the organization are not yet fully aware of this issue, or that they have not really "thoroughly understood the nature of the issue."
Microsoft
has a lot of really smart people — from Bill Gates and Steve Ballmer
right on down the line. But they are human, and they sometimes make
human mistakes. Sometimes it's worse than that, and as a company
they're stubborn in the face of some really bad decisions. Like
script-enabling their eMail clients so the virus du jour, like
Melissa, can impersonate the user and happily eMail itself across the
Internet to everyone in our address books.
SERIOUSLY DUMB IDEA in the works from Microsoft in Windows XP. I regret my silence when scripting was being added to eMail. It was the dumbest thing I had ever seen, but I didn't care since I use Eudora. So I didn't work to make the world take notice. Now eMail viruses are born daily to travel the Internet at light speed. And it could have — should have — been prevented.
From a recent SANS Security article (See the Security Editor's Note) This time, with the disaster of Windows XP support for "RAW SOCKETS" looming, there is still time to get Microsoft to yank it out. But as the correspondence below demonstrates, I have not yet managed to reach the right people or convince them that they must.
access to any Unix sockets programmer.
tool. They were NEVER INTENDED to be shipped in a mass-market consumer operating system.
Socket support has been a silent blessing that has undoubtedly contributed hugely to the stability of the global Internet of the past.
applications from gaining "Raw" access to the Internet will be MUCH harder to exploit.
hackers to find new ways into those machines — AND THEY WILL. Then users of Windows XP machines will become the most sought-after target for penetration.
hacker's dream come true.
| ||||||||||||||||||||||
|
| Greg was terrific about following up. I received a few progress reports as my note went through "channels". Then a couple of days later I received the following complete reply: |
|
| I
will respond, in detail, to these points Microsoft has raised. But
first I would like to raise and respond to some of the other questions
raised early in this controversy . . .
In fact, while discussing the OS Fingerprinting capabilities of his well-known "nmap" Internet scanner, nmap's author Fyodor, has this to say about nmap's detection of Windows versions:
If you read through Fyodor's fingerprinting description, you will see that nmap is a superlatively sensitive detection tool that can generally sense even the tiniest changes in the implementation of a system's TCP/IP stack. (Fyodor is certainly a "hacker" in the truest and most positive sense of the term.) Yet Microsoft's stack apparently never changed . . . until it suddenly changed completely. Several people have been quoted in the press defending Microsoft's stance by simply stating that "following standards is a good thing". In this context it is important to recognize that "Unix Sockets" is simply a "specification"; it has never been ANY sort of recognized "standard". For this reason, the proper way to view the past situation, is that the traditional Windows Sockets system implemented only as much of the Raw Sockets portion of the full Berkeley specification as was useful and required for Windows application software.
exactly right for a consumer operating system. I agree that following good and safe SPECIFICATIONS can be a good thing. But it seems to me that blindly following ANY recipe, whether it's a specification or a standard, and lacking an understanding and independent evaluation of its role in the intended application, is tantamount to replacing your own judgement with someone else's. For a well-informed person, abdicating responsibility is not always a good thing. Perhaps these people have never actually programmed the Windows Sockets system (as I have extensively). There is very little about Microsoft's Sockets — with their wild extensions (which I love by the way) — that follows the Berkeley specification. So the truth is, that either with or without full Raw Socket support, Windows Sockets never has been, and never can be "standard".
These people miss the essential aspect of "scale". If Microsoft were going to sell only a few thousand copies of Windows XP, I would not be wasting either your time or mine with this entire issue. But whereas Windows 98 and Windows ME have been largely uninteresting upgrades, Microsoft has loaded so many new goodies into WinXP that it will make for a compelling Christmas season.
future, Windows XP is going to become THE generic consumer personal computer operating system. Therefore, my concern is with the DEFAULT feature-set of the system and with the probable size of that feature-set's installed base. Sure, I wish that Windows 2000 were also "Raw Sockets Neutered" so that malicious hackers could not assume that all Windows 2000 machines were exploitable. I have no problem with the idea of an after-market add-on download pack from Microsoft, or of making the "deluxe stack" available in a Windows XP resource kit or MSDN subscription. It is the idea that EVERY CONSUMER MACHINE will have such dangerous capabilities that are NOT NEEDED AT ALL for Internet connectivity, that strikes me as being SO unnecessarily dangerous and . . . ultimately . . . dumb dumb dumb!
The beauty of "network egress filtering" is that each ISP becomes responsible for curtailing the IP spoofing of their own users. As I explain on my (still unfinished) DoS pages, once a forged packet "gets loose" from the ISP, and out onto the Internet, the task of tracking it back to its source is essentially impossible. The only opportunity to "block and drop" a spoofed packet is while it's still within the ISP's local network where it is EASILY identifiable as invalid and forged. Once that packet "egresses" onto the main Internet backbone, it's too late.
I believe that proponents of ISP network egress filtering are COMPLETELY correct. I have stated this at the conclusion of my previous page describing the Wicked DDoS Attacks. My announced plans for "Spoofarino", a free, user-oriented utility for encouraging ISP accountability for the lack of egress filtering, has already been discussed by the computer press. Today, the practice of network egress filtering is more the exception than the rule, but we can hope that it will be widely adopted as these issues attain increasing visibility in the future. However, this potential for an improvement in the Internet's infrastructure notwithstanding, it is important to recognize that . . .
While
egress filtering will be a good thing once it exists, it fails to solve
the problems of Denial of Service attacks in two ways: As this analysis demonstrates, network egress filtering is undoubtedly a good thing for the long term future of the Internet. But it does not, and can not, provide a cure-all solution to the problem of the Internet protocol abuse promoted by the existence of Windows XP's full Raw Socket support.
I will summarize what I read as Microsoft's stated position, point-by-point, and reply to each in turn:
Microsoft's Position:
HUH?!!
On Friday, June 8th, the TechNet page referenced above states: VMS, Unix, Mac OS X, and even in previous versions of Windows." And in their first reply to me, shown above:
The
following three examples provide concrete evidence of Microsoft's
apparent confusion over the issue of full Raw Socket support in
previous versions of Windows:
How
much more plain can that be? Windows 9x/ME and WinNT DO NOT HAVE the
Raw Socket capability to spoof the machine's actual IP address. This
was only added into Windows 2000 and is now being carried down into the
consumer market by Windows XP.
Here,
located on the "megasecurity" hacker site (provided with their
knowledge and permission), is the entire "readme" page for this typical
Windows DDoS attack tool. Note that it is not currently useable on any
consumer-grade Windows systems . . . but Microsoft's XP will soon be changing that, to the delight of malicious hackers everywhere:
While
you're at the megasecurity site, take just a moment to browse through
their catalog of the Trojans which will soon be competing for space on
Windows XP hard drives:
Of particular interest is the included "Attack" program which, according to that program's readme.txt file,
currently only runs under "w2k". Why? Because Windows 2000 is the only
Windows operating system that currently supports full Raw Sockets. But
as we all certainly know by now, this will soon change.
Under the "How does it work?" section, the author explains: Right.
This
author is describing a classic SYN flooding attack using a spoofed
Source IP. NO PRIOR VERSION OF WINDOWS allows its applications to
arbitrarily generate Internet packets. As this example demonstrates,
deliberately invalid — and malicious — SYN packets can NOT be generated
unless the application is running on Windows 2000 . . . or, soon, Windows XP.
This sample highlights another interesting aspect of Microsoft's poor judgement in this matter:
The
threat of attacks is NOT ONLY from surreptitiously installed
remote-control Zombie/Bot Trojans, but also from PC hobbyists who will
soon be able to gleefully launch untraceable spoofed IP SYN-flooding
attacks from the comfort of their own bedrooms. Presumably after
finishing their homework.
The
typical teenage hacker has not had access to Windows 2000. He or she
has been limited to playing video games on Windows 95/98/ME. But this
Christmas will change all that: When "Junior" asks Mom and Dad if he
can get an upgrade to the new really cool Microsoft Windows XP for
Christmas, Mom and Dad will smile and nod. "What a GREAT idea!" they
think to themselves.
Yeah. Great.
Trinoo
was such a successful attack tool over on the *NIX platforms, that it
was "ported" to the Windows environment under the name: WinTrinoo.
But, of course, WinTrinoo's malicious capabilities are somewhat limited under Windows. Unlike its Unix cousin, WinTrinoo can neither spoof source IPs, nor generate SYN flooding attacks.
You KNOW that WinTrinoo's authors know how to spoof source IPs and
generate SYN floods. They did it for Trinoo. So why doesn't WinTrinoo
have the same power under Windows? You know why: Because Windows has
traditionally lacked support for the full Raw Sockets specification.
Next year, after "The XP Christmas of Death" has passed, tens of millions of home PC's will be happily running Windows XP. How many minutes do you think it will take for "WinTrinoo2" to arrive on the scene and for it to take full advantage of XP's Unix-style full Raw Socket support?
So now, in light of what you've just seen, reconsider the intent behind Microsoft's summarized position, as documented above:
versions of Windows had support for Raw Sockets." What are they thinking up there in Redmond? I hope it is clear to you, in light of this little bit of evidence (there's an endless amount more), that the currently planned release of Windows XP into the consumer market, represents a crucial mistake. And given that Microsoft is fully aware of this, a shocking example of corporate hubris. |
| NEXT |
|
This quote is taken directly from Microsoft's TechNet page referenced above:
From the TechNet Page: We have just examined the obfuscation that was apparently intended at the end of that quote. (Regarding the applicability of full Raw Sockets to previous versions of Windows.) I hope you're no longer fooled by that. Let's look at the rest of it. "If it were, the explosion of DDOS attacks should have already occurred..." Perhaps Microsoft hasn't been reading about the rapid rise (explosion) in the number of DDoS attacks which is already occurring. One must wonder how they could be unaware of this since they have, themselves, been frequent targets of those attacks. Furthermore, they must know, as I demonstrated above, that the widespread availability of Linux and Unix, with their "system-level functions to manipulate data packets" are clearly responsible and are a "critical factor" in the number of DDoS attacks.
number of hobbyist-owned Unix and Linux boxes — often configured insecurely then compromised with Trojans — that we are now seeing a rapid growth in the number of DDoS attacks. Microsoft is about to massively escalate this problem! Although it is not completely clear what message Microsoft intended to convey with that quote, what they APPEAR to be saying here is something along the lines of:
. . . so why shouldn't we?" Assuming that this is what that quote was trying to say, it raises a good question which is worth exploration: As we have seen, it is indeed unfortunate that "everyone else" has full Raw Socket support. The Internet has already been suffering the consequences. That problem is certainly going to grow with time and needs to be dealt with as well. The fact that Microsoft was not the first to make this crucial mistake on the Internet in no way reduces their now-fully-informed responsibility to prevent their negligent compounding of the problem. The installed-base of consumer Windows operating systems dwarfs that of all other platforms combined. In shipping their Windows XP system, squarely targeted at the home and small office user, tens of millions of existing Windows platforms which have never had full Raw Socket support, will be upgraded overnight into powerful Internet attack platforms. And all new computers sold after Windows XP's release will have that built-in.
From the TechNet Page: That is absolutely true . . . and absolutely irrelevant. Every one of the three concrete examples we looked at first demonstrated that — in actuality — the lack of the DEFAULT AVAILABILITY of full Raw Socket support in traditional versions of Windows, completely prevented that malicious tool from gaining access to IP spoofing and TCP flooding capability. We KNOW that they all wanted it. Trinoo has it under Unix and Linux, but WinTrinoo doesn't under Windows. The other program examples apologized that they were only useable under Windows 2000 because of W2K's support for full Raw Sockets.
COULD be accomplished in theory, and what IS ACTUALLY ACCOMPLISHED in practice. Operating system kernel-level "packet drivers" are freely available on the Internet. Microsoft even provides a (buggy) sample of such a driver in their own "Platform SDK" (A sample kit for Windows developers.) But these have existed for years and have never been employed by any of the popular malicious tools. The reason for this is that it has never been nearly as simple as Microsoft makes it sound. Those solutions tend to be operating system version dependent and difficult to reliably install — especially remotely. As a result, and despite what might be possible, all of the evidence demonstrates that malicious tools exploit the interfaces provided by the native operating system. The addition of full Raw Socket support to the DEFAULT Windows XP consumer product guarantees that the next-generation Windows-hosted tools of mass malicious exploitation will be far more powerful than any previously designed for today's Windows operating system. It's just that simple. How could Microsoft NOT see that?
From the TechNet Page: Wrong. The REAL ISSUE is that Windows XP puts an operating system in the hands of the consumer which allows ANY SIMPLE APPLICATION PROGRAM — whether installed by a malicious hacker or used by the system's owner — to trivially generate sophisticated source IP spoofing Denial of Service (DoS) TCP SYN floods. None of Microsoft's previous, unmodified, consumer-targeted Windows operating systems allowed this. This is a huge change for the worse. Remember "Junior" whom we met awhile back when he asked his parents for a Windows XP upgrade for Christmas? Let's take a look at what "Junior" is up to after he returns to school from Christmas vacation . . .
It is a virtual certainty that applications such as the hypothetical "NukeEmNow.exe" will be written for Windows XP, and that those applications will be used by malicious individuals of ALL ages. (I didn't mean to single-out teenagers.) It is worth noting that since TCP "SYN" packets are extremely small (60 bytes) compared with data-carrying packets (1500 bytes), many more SYN packets can be sent per second than data packets. This gives a SYN flooding machine more "packet potency" than one which is attempting to transfer valid data. The consequence of this, is that a single SYN-flooding machine can completely knock out any other machine connected at the same or lesser speed. Coupled with Windows XP, and a breed of cyber-war toys like the still-hypothetical "NukeEmNow.exe" described above, we can expect "one-on-one" cyber-battles between individuals. If someone doesn't like what someone else says or does, they are too easily blown off the Internet. Let me say it again: This is all COMPLETELY UNNECESSARY since no Windows applications have ANY need for full Raw Socket support. No VALID use exists outside of an Internet research setting. Raw Sockets were only included by the original Berkeley designers for Internet protocol research. In a consumer computer system, they will only be exploited for malicious purposes. So, as we see, the "real issue" (to quote Microsoft) is NOT whether the attacker can run hostile code on another user's computer. I submit that the "real issue" is whether a personal computer can be much too easily programmed to generate untraceable and maliciously damaging Internet traffic. Until now, for Windows, that answer was no, and as a direct consequence it was never done.
malicious traffic. You already know what will happen.
Here is a simple fact:
secure, consumer, personal computer. Security is black and white. Either you are secure and protected, or you're not. Strange as it might seem at first, I don't blame Microsoft for their demonstrated inability to build a perfectly secure personal computer. After all, it's not possible. But I do hold Microsoft responsible for continually marketing and selling something they can never produce. And they MUST be held responsible for the consequences of believing their own marketing and press. Ask any real security expert, like Bruce Schneier of Counterpane Internet Security. They will tell you flat out that it's an impossible task to secure a personal, consumer, computer. Why does Microsoft continually insist otherwise? Because it is what people desperately want to hear, and desperately want to believe. Well . . . it's not possible. Microsoft's software has NEVER been secure, and NEVER will be. With each generation of feature-rama upgrade, it becomes more and more complex, and less and less understandable. There can not be anyone left at Microsoft whose mind can still grasp the technical details of the entire system. They had to give that up with MS-DOS. Microsoft's lack of security foresight is single-handedly responsible for creating the eMail virus. Their consumer operating systems — as well as their high-end server platforms — are notoriously insecure.
Just two weeks ago (May 23rd, 2001) . . .
Whoops. But, patching Windows doesn't always work either . . .
From the SANS Institute NewsBites service And then there's what the hackers know . . .
From the SANS Institute NewsBites service How, then, can anyone accept Microsoft's defense for adding incredibly exploitable and utterly unnecessary Internet technology into their base consumer-level system as: "Don't worry, THIS one will REALLY be secure." ?? You MUST KNOW that not long after its release, the world will begin finding huge security holes in Windows XP. Oh sure, Microsoft will issue patches. Then the users will be blamed for not installing them in a timely fashion. What's WRONG with those damn users anyway? And even if, against all logic and our wealth of experience, you're on the fence with this question . . . WHAT IF MICROSOFT IS WRONG? There is just too much riding on the issue of the security of this completely unproven new system. We lose NOTHING if I am wrong about this and if Windows XP has its full support for Raw Sockets removed. But . . .
Speaking of which, this just in . . .
secure consumer personal computer.
How many people complain that the annoying "Comet Cursor" keeps getting installed into their computer whenever they visit certain web sites? That's Comet Cursor's CODE being downloaded and run without the user's knowledge or permission. Microsoft's default web browser settings — which the typical user uses without a second thought — allows all manner of similar remote web-based exploits. What happens when a Windows XP user innocently surfs to a site that was set up to take over those machines? When I reverse-engineered the Aureate/Radiate advertising Spyware, to create the OptOut spyware detector and removal tool, I mentioned that it would be trivial for any malicious hacker to commandeer the Aureate Trojan and cause it to do their bidding. One line added to an innocuous and unprotected file, will cause any of the more than 30 million Aureate Trojans to "phone home" to a different server. From there it's trivial to have the Trojan accept a file to download and then run it. And if all that's not worrisome enough, the Aureate Trojan undetectably runs within the Internet Explorer browser process; this lets it slip past the system's firewall by trading on the browser's Internet access permissions. So much for Windows XP security. As any of you who run a personal firewall with "noisy logging" know, routine scans for the PC Anywhere remote control utility are STILL occurring on the Internet. Why? Because people installed PC Anywhere in their machines to give them remote access across the Internet. The only problem was, a great many of these people never bothered with a password. Thus, anyone could scan the Internet to find a machine running the "PC Anywhere" Trojan and "own it". So much for the "security" of that machine. As you can see from these examples, the goal of an "absolutely" secure personal computer for the masses is impossible to achieve. It's true that exercising extreme care and caution can result in "a more secure PC". But that can only be achieved in degree, never absolutely. For example, even Windows 95 could be quite secure if the user were careful about its configuration and diligent about its use. But the average consumer can not be expected to appreciate the subtle and complex nuances of Internet security — especially when being stalked, tricked, and seduced by malicious hackers. Typical consumer computer users will tend to do insecure things. There's no practical means to prevent that, since that's what they want to do. More than anything else, personal computer users want freedom. Windows NT and 2000 are supposedly "secure" operating systems, yet malicious Russian hackers have been breaking into those machines left and right, then stealing consumer credit card data. Has anyone ever supported the contention that WinNT and Win2000 are immune to viral infection? Has anyone ever contended that? I've never heard any such thing because we all know it's ridiculous. We all know that no Windows system is inherently safe or secure. The truth is, that can NEVER change due to the customer-base these systems have been built to satisfy.
|
| Last Edit: Oct 06, 2003 at 13:31 (467.60 days ago) | Viewed 183 times per day |
|
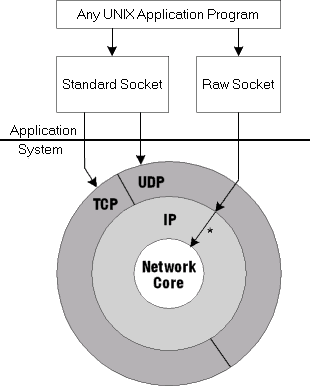 Circa
1981 — The Computer Systems Research Group (CSRG), at the University of
California at Berkeley, first mated the Unix operating system to the
Internet. This was done by implementing the Internet protocols and
creating a so-called "TCP/IP Stack" for Unix. This is shown as
concentric regions in the diagram to the left.
Circa
1981 — The Computer Systems Research Group (CSRG), at the University of
California at Berkeley, first mated the Unix operating system to the
Internet. This was done by implementing the Internet protocols and
creating a so-called "TCP/IP Stack" for Unix. This is shown as
concentric regions in the diagram to the left.
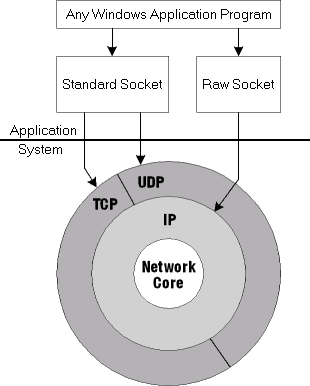 Compare
the schematic diagram we've been looking at above, to Microsoft's
traditional Windows Sockets (WinSock) implementation to the left.
Compare
the schematic diagram we've been looking at above, to Microsoft's
traditional Windows Sockets (WinSock) implementation to the left.